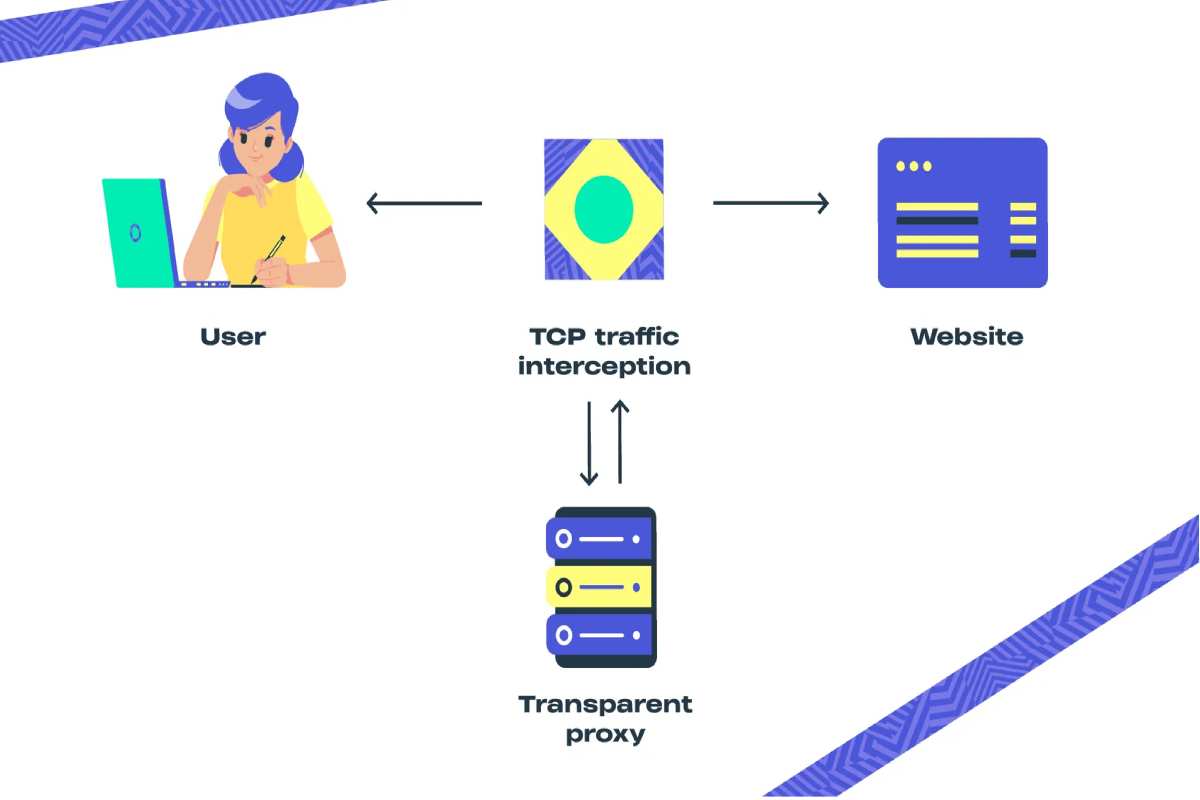
Understanding the basics of a transparent proxy server is easier than it sounds. Imagine walking through a glass tunnel – you see everything clearly, yet you’re subtly guided in a particular direction. That is exactly how a transparent proxy works. It acts as an invisible middle layer between your device and the internet, quietly processing requests without altering the way you interact online. Unlike other types of proxies, it doesn’t hide your identity or change your IP address. Instead, its main purpose is control, monitoring, and sometimes content filtering.
How a Transparent Proxy Server Works
When you request access to a website, your device usually connects directly to that server. A transparent proxy server steps in between this connection, intercepting and forwarding your request without any need for manual configuration on your side. It earns its name “transparent” because users typically don’t even realize it’s there – all traffic is automatically redirected through it.
For instance, businesses and schools often rely on transparent proxies to monitor activity, block harmful sites, or ensure bandwidth efficiency. Since users don’t have to configure settings, it reduces friction while still giving administrators the control they need. Think of it as a traffic officer standing at a crossroads, ensuring the flow moves smoothly and according to the rules.
Key Benefits of Transparent Proxy Servers
The appeal of transparent proxies lies in the balance between visibility and control. While they don’t provide anonymity, they deliver practical advantages that suit specific environments. Some of the notable benefits include:
- Ease of use: No setup is required by the user, as the proxy intercepts traffic automatically.
- Content filtering: Perfect for organizations that want to block or allow certain websites.
- Monitoring capabilities: Useful for tracking browsing habits, employee activity, or even detecting policy violations.
- Bandwidth management: Helps prioritize traffic, ensuring critical tasks like video conferencing remain smooth.
This combination of features makes transparent proxies ideal for workplaces, public Wi-Fi, or educational institutions where control outweighs the need for personal privacy.
Where Transparent Proxies Are Commonly Used
Transparent proxy servers thrive in structured environments where oversight is crucial. Corporations use them to enforce internet usage policies and reduce security risks. Schools rely on them to block inappropriate or distracting content, ensuring students remain focused on learning. Public libraries and cafés might use them to prevent access to unsafe sites while still offering free internet access.
In addition, internet service providers (ISPs) sometimes deploy transparent proxies to cache popular content, speeding up access for their customers. By temporarily storing frequently visited data, they cut down on redundant bandwidth usage and improve overall efficiency.
Comparison of Transparent Proxy vs Other Proxies
Although transparent proxies have a distinct role, it’s important to understand how they differ from other types. Below is a simple comparison:
| Feature | Transparent Proxy | Anonymous Proxy | Elite Proxy |
| User Awareness | Hidden | Requires setup | Requires setup |
| IP Masking | No | Yes | Yes |
| Main Use Case | Monitoring, filtering | Privacy, browsing | Maximum anonymity |
| Ease of Implementation | Very easy | Moderate | More complex |
As the table shows, transparent proxies sacrifice anonymity in favor of seamless integration and monitoring control. They are not a tool for privacy but rather a mechanism for management.
Practical Scenarios and Real-World Examples
Think of a transparent proxy as a schoolteacher watching over a classroom. The teacher doesn’t stop students from doing their work but ensures they stay on the right track, guiding or correcting behavior when necessary. Similarly, when you log in to a café Wi-Fi that automatically blocks adult content or pirated sites, that’s a transparent proxy at work.
Another example is corporate offices. Employees may not realize their traffic is being filtered or cached, yet the IT team uses the proxy to prevent data leaks, malware infections, and time wasted on non-work-related browsing.
If you’re curious to explore how these proxies operate in detail, you can visit this link, which provides further insight into their technical features and applications.
Advantages and Limitations to Consider
While transparent proxies offer efficiency and control, they also come with limitations. They are not designed for privacy seekers. Since your IP address remains visible, your browsing activity can still be tracked by external sites. Moreover, because users are often unaware of being monitored, this can raise ethical and legal concerns in some contexts.
On the positive side, they remain one of the simplest ways to enforce digital policies without requiring any action from users. This makes them a favorite for network administrators who need oversight with minimal disruption.
Conclusion: The Subtle Power of Transparent Proxies
A transparent proxy server is best thought of as a silent gatekeeper. It doesn’t interfere with your browsing experience directly but quietly ensures that rules are followed, resources are managed, and access remains safe. From businesses to schools to public hotspots, these proxies provide an efficient way to blend seamless user access with much-needed oversight. While they are not built for privacy or anonymity, their value lies in structure and stability, giving administrators an invisible yet powerful tool to manage digital environments.